Information Security
Information Security
Information Security Management System (ISO27001)
ISO/IEC 27001 is the internationally recognised standard for effective information security management. The ISO 27001 Gap Analysis service is a specialised, in-person review of your information security regime that will give you a high-level overview of what you need to do to achieve certification to ISO 27001.
ISO 27001’s breadth of applicability can make it difficult for organisations to determine how to apply the Standard effectively and economically.
Our consultancy team has helped companies prepare for ISO 27001 certification. Get customised, personal advice from an experienced ISO27001 implementation specialist with our ISO 27001 Gap Analysis and Audit service.
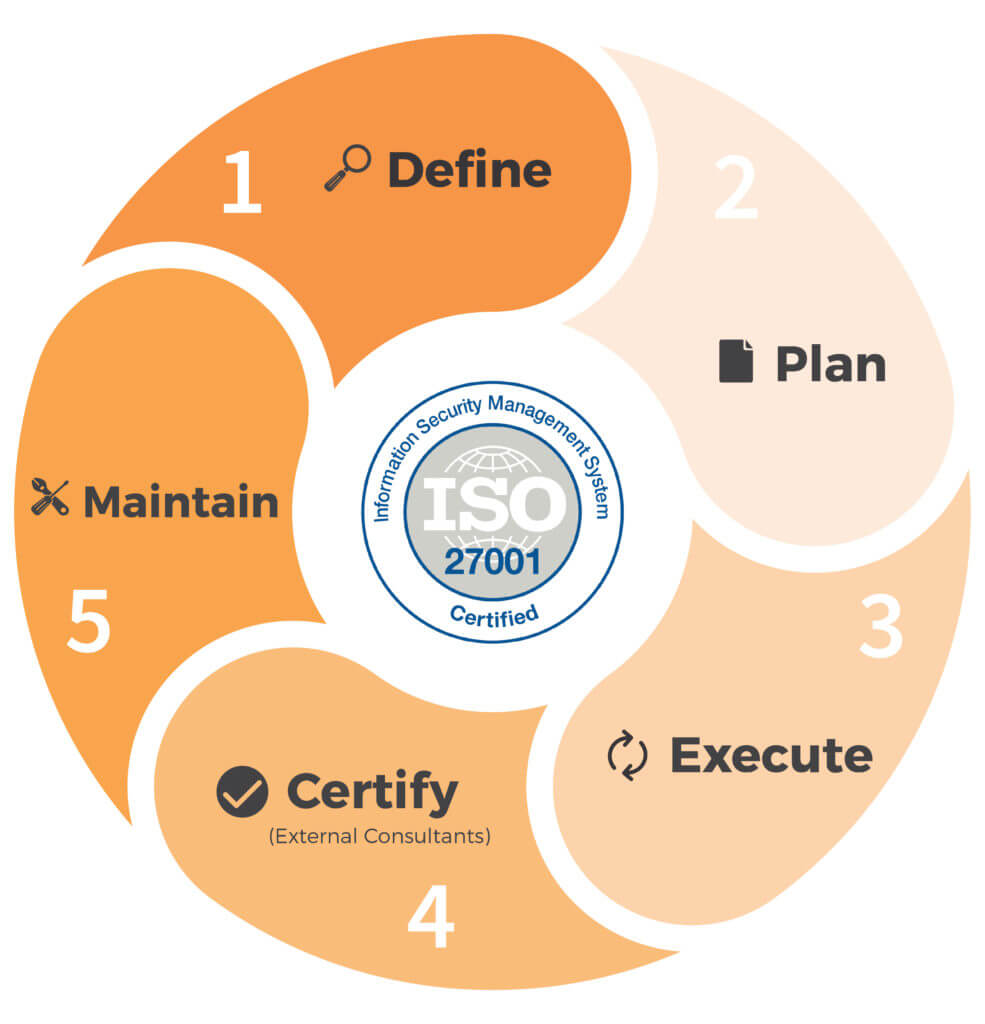
Information Security Management System (ISO27001)
ISO/IEC 27001 is the internationally recognised standard for effective information security management. The ISO 27001 Gap Analysis service is a specialised, in-person review of your information security regime that will give you a high-level overview of what you need to do to achieve certification to ISO 27001.
ISO 27001’s breadth of applicability can make it difficult for organisations to determine how to apply the Standard effectively and economically.
Our consultancy team has helped companies prepare for ISO 27001 certification. Get customised, personal advice from an experienced ISO27001 implementation specialist with our ISO 27001 Gap Analysis and Audit service.


Privacy Regulations (GDPR, CCPA, KVKK etc.)
New privacy laws and incidents of privacy violations, identity theft and personal information mismanagement have increased regulatory and consumer pressure to prevent disclosure or compromise of personally identifiable and sensitive information. The business impacts of failure – on both long-term relationships and value – have elevated the issues of privacy, security and information risk management to the board and senior executive level at many companies. Addressing privacy issues on a global, basis and in a consistent and cost-effective manner is crucial to maintaining a competitive edge in today’s global economy.
Secureway offers a wide range of privacy and data protection services, and can help you;
- Build an integrated, privacy compliance and risk framework in line with Privacy requirements
- Conduct privacy, security and/or identity theft prevention assessments
- Perform personal information inventories of the business processes and locations that handle high-risk or regulatory sensitive information
- Build privacy program business plans, budgets and roadmaps
- Design and implement solutions to address key risks and areas of noncompliance; enhance data classification scheme and technical and physical security safeguards; re-architect global data flows; design automated vendor privacy and security oversight programs
- Prepare for GDPR and other global compliance solutions with implementation of ISO27001 and ISO27018
- Provide DPO as a service for continuous compliance
Privacy Regulations (GDPR, CCPA, KVKK etc.)
New privacy laws and incidents of privacy violations, identity theft and personal information mismanagement have increased regulatory and consumer pressure to prevent disclosure or compromise of personally identifiable and sensitive information. The business impacts of failure – on both long-term relationships and value – have elevated the issues of privacy, security and information risk management to the board and senior executive level at many companies. Addressing privacy issues on a global, basis and in a consistent and cost-effective manner is crucial to maintaining a competitive edge in today’s global economy.
Secureway offers a wide range of privacy and data protection services, and can help you;
- Build an integrated, privacy compliance and risk framework in line with Privacy requirements
- Conduct privacy, security and/or identity theft prevention assessments
- Perform personal information inventories of the business processes and locations that handle high-risk or regulatory sensitive information
- Build privacy program business plans, budgets and roadmaps
- Design and implement solutions to address key risks and areas of noncompliance; enhance data classification scheme and technical and physical security safeguards; re-architect global data flows; design automated vendor privacy and security oversight programs
- Prepare for GDPR and other global compliance solutions with implementation of ISO27001 and ISO27018
- Provide DPO as a service for continuous compliance

Information and Communication Security Guide
Within the scope of the Presidential Circular dated 06.07.2019 and numbered 2019/12, which includes Information and Communication Security measures that must be followed by public institutions and businesses providing critical infrastructure services, the preparation of the “Information and Communication Security Guide”, which was initiated under the coordination of the Presidency of the Presidency Digital Transformation Office, was completed and on 24.07.2020. has been approved.
Information and Communication Security measures that must be followed by public institutions and businesses providing critical infrastructure services in order to reduce and neutralize the security risks encountered in information systems and to ensure the security of critical data that may threaten national security or cause disruption of public order, especially when its confidentiality, integrity or accessibility is impaired. The circular has been an important step towards increasing the level of information security throughout the country in terms of legal regulation.

It is obligatory to comply with the precautions given in the Guide in the existing and newly established information systems in all public institutions and organizations and enterprises providing critical infrastructure services. Existing information technology infrastructures will be gradually harmonized with these principles within the framework of the plan in the Guide, taking into account the security level priorities.
Critical infrastructure sectors are included in the 2020 – 2023 National Cyber Security Strategy and Action Plan as “Electronic Communication”, “Energy”, “Water Management”, “Critical Public Services”, “Transportation”, “Banking and Finance”.
A compliance plan* has been created in the Guide for institutions, organizations and businesses within the scope of the Information and Communication Security Guide.
The studies to be carried out within the scope of the guideline compliance plan are given below:
Between 1 – 6 months: Asset Group Criticality Determination and Gap Analysis Studies
Between 6 – 18 months: 1. Implementation of Level Measures
Between 6 – 21 months: 2. Implementation of Level Measures
Between 6 – 24 months: 3. Implementation of Level Measures
It is important for the institutions, organizations and businesses within the scope to take into account the calendar in the compliance plan, in terms of carrying out the harmonization process in a planned manner and completing it on time.
Asset Groups
The asset groups in the Guide are defined under six main headings and the relevant headings are given below.
- Network and Systems
- Apps
- Portable Devices and Media
- IoT Devices
- Employee
- Physical Spaces
In order to determine the criticality level of assets, asset groups should be defined in accordance with the issues on page 22 of the Guidelines. More than one asset group can be defined for each asset group title.
Audit Scope
Correct planning is important for the successful conclusion of the audit. Therefore, Secureway will determine the services, infrastructure and locations subject to the audit with a project kick-off meeting attended by the senior management of the Institution and the relevant unit managers and will evaluate the applicability of each BIG control item to this structure.
Secureway will ensure that the scope that will be the basis for BIG compliance and auditing is correctly determined by meeting with the relevant units of the Institution. While determining the scope, all processes and components related to the Institution’s business processes, campuses, data centers, systems, employees, service providers, transmission, operation, storage, destruction of information and affecting the security of the Institution’s infrastructure will be taken into account.
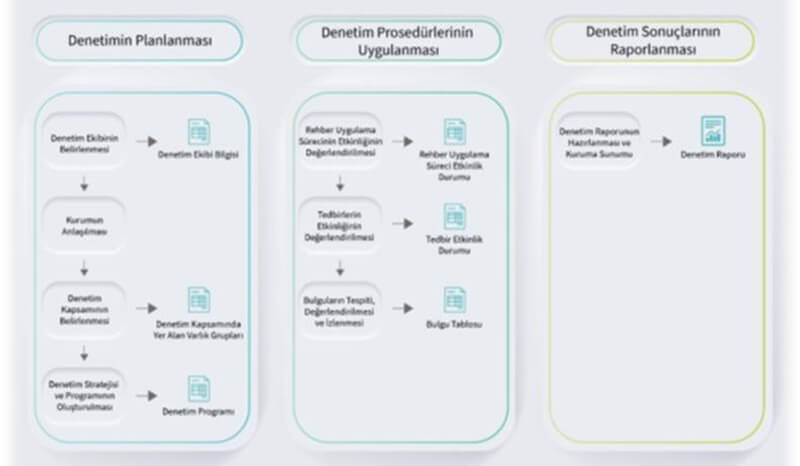
Methodology
The methodology to be applied in the guideline compliance audit; It proceeds in three main process axes: planning the audit, implementing the audit procedures and reporting the audit results. The main objective of the audit is to measure the following criteria.
Information and Communication Security Guide
Within the scope of the Presidential Circular dated 06.07.2019 and numbered 2019/12, which includes Information and Communication Security measures that must be followed by public institutions and businesses providing critical infrastructure services, the preparation of the “Information and Communication Security Guide”, which was initiated under the coordination of the Presidency of the Presidency Digital Transformation Office, was completed and on 24.07.2020. has been approved.
Information and Communication Security measures that must be followed by public institutions and businesses providing critical infrastructure services in order to reduce and neutralize the security risks encountered in information systems and to ensure the security of critical data that may threaten national security or cause disruption of public order, especially when its confidentiality, integrity or accessibility is impaired. The circular has been an important step towards increasing the level of information security throughout the country in terms of legal regulation.
It is obligatory to comply with the precautions given in the Guide in the existing and newly established information systems in all public institutions and organizations and enterprises providing critical infrastructure services. Existing information technology infrastructures will be gradually harmonized with these principles within the framework of the plan in the Guide, taking into account the security level priorities.
Critical infrastructure sectors are included in the 2020 – 2023 National Cyber Security Strategy and Action Plan as “Electronic Communication”, “Energy”, “Water Management”, “Critical Public Services”, “Transportation”, “Banking and Finance”.
A compliance plan* has been created in the Guide for institutions, organizations and businesses within the scope of the Information and Communication Security Guide.
The studies to be carried out within the scope of the guideline compliance plan are given below:
Between 1 – 6 months: Asset Group Criticality Determination and Gap Analysis Studies
Between 6 – 18 months: 1. Implementation of Level Measures
Between 6 – 21 months: 2. Implementation of Level Measures
Between 6 – 24 months: 3. Implementation of Level Measures
It is important for the institutions, organizations and businesses within the scope to take into account the calendar in the compliance plan, in terms of carrying out the harmonization process in a planned manner and completing it on time.
Asset Groups
The asset groups in the Guide are defined under six main headings and the relevant headings are given below.
- Network and Systems
- Apps
- Portable Devices and Media
- IoT Devices
- Employee
- Physical Spaces
In order to determine the criticality level of assets, asset groups should be defined in accordance with the issues on page 22 of the Guidelines. More than one asset group can be defined for each asset group title.
Audit Scope
Correct planning is important for the successful conclusion of the audit. Therefore, Secureway will determine the services, infrastructure and locations subject to the audit with a project kick-off meeting attended by the senior management of the Institution and the relevant unit managers and will evaluate the applicability of each BIG control item to this structure.
Secureway will ensure that the scope that will be the basis for BIG compliance and auditing is correctly determined by meeting with the relevant units of the Institution. While determining the scope, all processes and components related to the Institution’s business processes, campuses, data centers, systems, employees, service providers, transmission, operation, storage, destruction of information and affecting the security of the Institution’s infrastructure will be taken into account.

Contact us
Please let us know
how we can assist
Secureway’s business philosophy is to provide the highest quality innovative solutions, total customer satisfaction, timely delivery of solutions and the best price performance available in the industry.
Our mission is to help you improve your security performance, reduce risks, make you more productive, less stressed and a little more confident.
Contact Form
Contact us
Please let us know
how we can assist
Secureway’s business philosophy is to provide the highest quality innovative solutions, total customer satisfaction, timely delivery of solutions and the best price performance available in the industry.
Our mission is to help you improve your security performance, reduce risks, make you more productive, less stressed and a little more confident.
